
Zoom’s security journey: Our 2024 bug bounty year in review
Zoom’s Bug Bounty Program incentivizes the discovery and responsible disclosure of security vulnerabilities. Here's a look at the past year's highlights.
Updated on April 25, 2022
Published on October 14, 2020

We’re excited to announce that starting next week, Zoom’s end-to-end encryption (E2EE) offering will be available as a technical preview, which means we’re proactively soliciting feedback from users for the first 30 days. Zoom users - free and paid - around the world can host up to 200 participants in an E2EE meeting on Zoom, providing increased privacy and security for your Zoom sessions.
We announced in May our plans to build an end-to-end-encrypted meeting option into our platform, on top of Zoom’s already strong encryption and advanced security features. We’re pleased to roll out Phase 1 of 4 of our E2EE offering, which provides robust protections to help prevent the interception of decryption keys that could be used to monitor meeting content.
To be clear, Zoom’s E2EE uses the same powerful GCM encryption you get now in a Zoom meeting. The only difference is where those encryption keys live.
In typical meetings, Zoom’s cloud generates encryption keys and distributes them to meeting participants using Zoom apps as they join. With Zoom’s E2EE, the meeting’s host generates encryption keys and uses public key cryptography to distribute these keys to the other meeting participants. Zoom’s servers become oblivious relays and never see the encryption keys required to decrypt the meeting contents.
“End-to-end encryption is another stride toward making Zoom the most secure communications platform in the world,” said Zoom CEO Eric S. Yuan. “This phase of our E2EE offering provides the same security as existing end-to-end-encrypted messaging platforms, but with the video quality and scale that has made Zoom the communications solution of choice for hundreds of millions of people and the world’s largest enterprises."
Zoom’s E2EE will be available as a technical preview next week. To use it, customers must enable E2EE meetings at the account level and opt-in to E2EE on a per-meeting basis.
How does Zoom provide end-to-end encryption?
Zoom’s E2EE offering uses public key cryptography. In short, the keys for each Zoom meeting are generated by participants’ machines, not by Zoom’s servers. Encrypted data relayed through Zoom’s servers is indecipherable by Zoom, since Zoom’s servers do not have the necessary decryption key. This key management strategy is similar to that used by most end-to-end encrypted messaging platforms today.
How do I turn on E2EE?
Hosts can enable the setting for E2EE at the account, group, and user level and can be locked at the account or group level. All participants must have the setting enabled to join an E2EE meeting. In Phase 1, all meeting participants must join from the Zoom desktop client, mobile app, or Zoom Rooms.
When would I use E2EE?
E2EE is best for when you want enhanced privacy and data protection for your meetings, and is an extra layer to mitigate risk and protect sensitive meeting content. While E2EE provides added security, some Zoom functionality is limited in this first E2EE version (more on that below). Individual Zoom users should determine whether they need these features before enabling this version of E2EE in their meetings.
Do I have access to all the features of a regular Zoom meeting?
Not right now. Enabling this version of Zoom’s E2EE in your meetings disables certain features, including join before host, cloud recording, streaming, live transcription, Breakout Rooms, polling, 1:1 private chat, and meeting reactions.
Do free Zoom users have access to end-to-end encryption?
Yes. Accounts joining directly from Zoom’s desktop client or mobile app, or from a Zoom Room, can join an E2EE meeting, or host one if enabled in account settings.
How is this different from Zoom’s Enhanced encryption?
Zoom meetings and webinars by default use 256-bit AES-GCM encryption for audio, video, and application sharing (i.e., screen sharing, virtual whiteboarding) in transit between Zoom applications, clients, and connectors. In a meeting without E2EE enabled, audio and video content flowing between users’ Zoom apps is not decrypted until it reaches the recipients’ devices. However, the encryption keys for each meeting are generated and managed by Zoom’s servers. In a meeting with E2EE enabled, nobody except each participant – not even Zoom’s servers – has access to the encryption keys being used to encrypt the meeting.
How do I verify that my meeting is using end-to-end encryption?
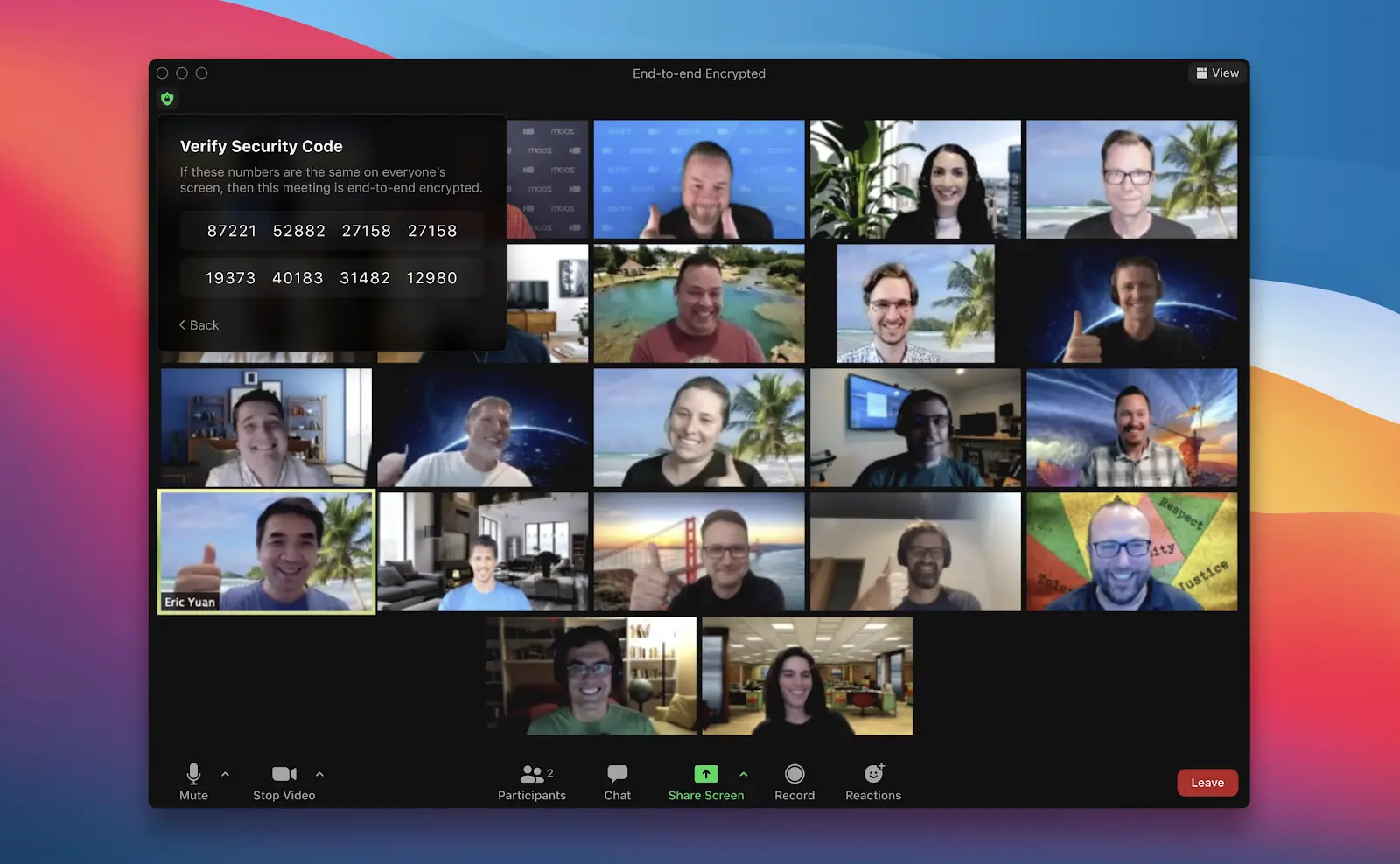
Participants can look for a green shield logo in the upper left corner of their meeting screen with a padlock in the middle to indicate their meeting is using E2EE. It looks similar to our GCM encryption symbol, but the checkmark is replaced with a lock.
Participants will also see the meeting leader’s security code that they can use to verify the secure connection. The host can read this code out loud, and all participants can check that their clients display the same code.
How will you continue to provide a safe and secure platform?
Zoom’s top priority is the trust and safety of our users, and our implementation of E2EE will allow us to continue to enhance safety on our platform. Free/Basic users seeking access to E2EE will participate in a one-time verification process that will prompt the user for additional pieces of information, such as verifying a phone number via text message. Many leading companies perform similar steps to reduce the mass creation of abusive accounts. We are confident that by implementing risk-based authentication, in combination with our current mix of tools — including our work with human rights and children’s safety organizations and our users’ ability to lock down a meeting, report abuse, and a myriad of other features made available as part of our security icon — we can continue to enhance the safety of our users.
What is the rest of the timeline for E2EE?
We plan to roll out better identity management and E2EE SSO integration as part of Phase 2, which is tentatively roadmapped for 2021.
To learn more about using end-to-end encryption and other security features for your Zoom meetings, visit Zoom’s security webpage.
Editor’s note: This blog post was edited on Aug. 3, 2021 to include the most up to date information on Zoom encryption.